The Big Data Paradox: Juggling Data Flows, Transparency And Secrets
Big Data is a captivating phenomenon in many respects, but is it clear what we mean by Big Data?
Big Data is a captivating phenomenon in many respects. Data are to this century what oil was to the previous one: a driver of growth and change. The interconnectedness of exponentially growing data flows entails great promises for personal, commercial, as well as governmental use. But, is it clear what we mean by Big Data? There are many perspectives on Big Data imaginable, and at the moment, there is no single accepted definition. Big Data can be looked upon from a technical, socio-technical, as well as governance level, either generically or in detail, and is considered both an opportunity and a threat (Figure 1 below). Change holds promises, but is by the same token unsettling and intimidating. From one perspective, the advent of Big Data ensures improved transparency from which society will greatly benefit. From another perspective, Big Data forebodes the horrifying perspective of an all-knowing, and possibly authoritarian, regime. In other words: Big Brother will be watching you … soon!
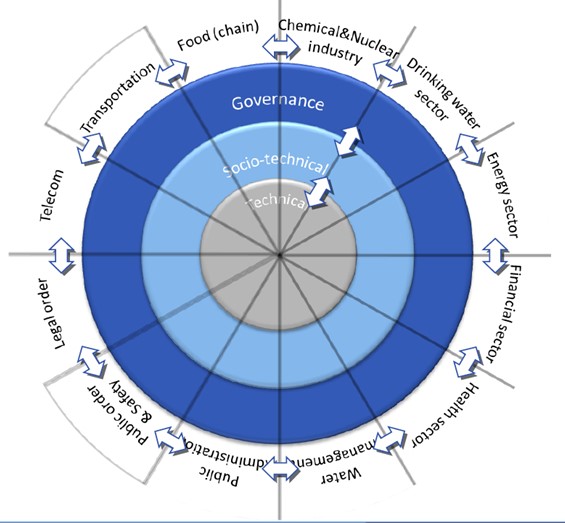
Figure 1: Conceptualization of Cyberspace. Source: Van den Berg et al. 2014, p. 2.
The attractiveness of data flows as a powerful means of security improvement, based upon (automated) pattern recognition, analysis and increased predictive value, is well recognized. This attractiveness from a security point of view has aroused suspicion regarding possible infringements on civil liberties. It is therefore closely monitored by e.g. human rights activists and privacy watchdogs. They fear that fundamental rights will be jeopardized by the increased leverage of the state in tracking its citizens for a range of purposes, e.g. maximizing tax returns, minimizing social benefit payments, countering radicalization, or punishing criminal behavior. Notwithstanding the validity of the mentioned purposes, these advocates stress that the position of the individual versus the state has deteriorated and therefore plead for more and better safeguards. This includes transparency and oversight when it comes to the handling of Big Data flows by the state in general, and the security and intelligence community in particular.
Big Data Developments: Increased Transparency and Secrecy
This blog highlights the complementarity and/or compatibility of seemingly opposed notions. Such a perspective conforms to the definition of a paradox as “a statement that is seemingly contradictory or opposed to common sense and yet is perhaps true.” This is illustrated by showing that the notions of transparency and secrecy do not exclude each other, but comprise two sides of the same coin.
In order to counter radicalism, terrorism and threats in general Dutch society at present seems to value a well-functioning intelligence and security apparatus more than before. This apparatus consists of a police force and military, complemented and assisted by the proportionate activities (as circumscribed by law) of the two Dutch intelligence and security services: AIVD and MIVD. The toolbox of these organizations naturally includes the full potential of the digital era exemplified in, for example, Big Data developments. Big Data, however, is by definition connected to a free and transparent flow of information. This does not seem to relate well to the behaviour of intelligence and security services.
However, the apparent incompatibility of transparency and secrecy is not absolute, even though it is commonly perceived and/or framed as such in the public debate. Recognition and awareness of this Big Data paradox will serve current and future discussions. This is exemplified by the (ongoing!) Dutch debate with regard to the new Intelligence Law of 2017.
Debating Secrecy
To a substantial degree, the intelligence law debate in the Netherlands centres around the technical possibilities of large-scale automated data communication interception and the risks involved in approval of such methods. In other words, the privacy versus security argument is at play here. When the Dutch government put its intelligence law proposal up for internet consultation, this resulted in 1,114 responses. Next to matters of oversight (both ex-ante and ex-post), the cost incurred by companies, and cooperation with foreign services, technical issues and their potential consequences were eagerly debated and subjected to criticism. A number of issues (in random order) received particular attention:
- Large-scale interception of cable communication;
- Search through large amounts of data;
- Automated access and analysis of databases;
- Obligating companies and organizations to decrypt communication.
The criticism on these issues boiled down to:
- matters of necessity, proportionality, and subsidiarity,
- question marks concerning privacy goals, and
- the technical impossibility of compliance.
This emphasizes the importance of a well-functioning oversight mechanism, given the fact that intelligence and security services already possess far-ranging powers by law regardless of the actual outcome of the intelligence law revision. Though governance encompasses more than oversight, the third layer within the cyber domain (Figure 1 above) thereby appears on the horizon as an important part of an indispensable system of checks and balances.
The intelligence law debate, however, has remained focused on the technical and, to a lesser extent, socio-technical layers, as can be seen from other contributions to the discussion. For understandable reasons the technically possible interception, collection and storage of huge amounts of data tickles people’s imagination. Catchphrases such as ‘select before you collect’, ‘collect before you select’ and even ‘select while you collect’ exemplify the main road taken by most researchers. A look at the reports of the Dutch Review Committee on the Intelligence and Security Services (Commissie van Toezicht op de Inlichtingen- en Veiligheidsdiensten, CTIVD) corroborates this. Twelve out of sixty-six investigative reports listed on its website deal with Signals Intelligence (SIGINT), or more precisely communication interception (tapping and/or hacking), storage and analysis. Viewing the content of a WRR-working paper on the use of Big Data by the MIVD and AIVD leads to a similar conclusion.
Paradoxes at Play: Transparency versus Secrets
The possibilities offered by the information revolution enable people to gather information and connect with each other at the speed of light. In its wake transparency has become the norm and is also expected from the state apparatus. However, enthused state bureaucracies are collecting more and more information from the lives of its citizens and show no inclination to keep fewer things secret. This translates into a privacy paradox and a transparency paradox. According to Broeders, most people claim to be worried about their privacy, but in (digital) practice they behave without concern for these worries. To this must be added the acceptance, or more likely neglect, that many (commercial) databases hide themselves in and behind computer applications that make digital life so comfortable. Citizens are thus becoming ever more transparent for the state, whereas it has become more difficult to identify what personal information which government agency possesses. In other words, the state is becoming less transparent.
The right to have secrets is part of the ‘social contract’ between citizens and the state. In a recent study, Paul Frissen pays attention to the fact that a democratic state (democratische rechtsstaat) keeps secrets in the interest of the welfare, well-being, and (self) development of its citizens. Being of a personal nature, these secrets are very much connected to privacy aspects. In addition, state secrets serve the purpose of state security, and the stability of society and democratic legal order. Frissen emphasizes that state success in the second domain requires the acquisition of secrets. In the Netherlands, these secrets are obtained with the help of special powers by ministerial approval without prior judicial review. Obviously, such state activities might seriously infringe upon people’s privacy and their liberties and, therefore, require supervision and oversight. This demands from the state to be strong and weak at the same time.
Paul Frissen maintains that the freedom of any citizen rests partly on his right to have secrets. To protect that right the state is obligated to prevent and counteract any attempt to undermine this. Paradoxically, this requires secrecy to a certain extent. Or, in his opinion, the legitimacy of the state to perform secretive acts is also based upon people’s right to have secrets. As long as the state protects this, it is entitled to have secrets of its own. In other words, to be legitimate the state needs to protect the secrets of its citizens, but to be effective the state needs secrets of its own, and … as much transparency of its citizens as possible.
Owing to Big Data flows and technology, ‘transparent citizens’ seem within grasp. Frissen distinguishes two elements within the earlier mentioned transparency paradox. First, total transparency as the societal norm precludes the existence of secrets. However, the concept of total transparency will ultimately rob a person of his individual freedom (e.g. to have scandalous thoughts or despicable opinions; in other words to be allowed to have secrets). The disturbing consequences have been eloquently fictionalized by writers like George Orwell in 1984 (1949), or more recently, Dave Eggers in The Circle (2013). Second, it has simultaneously motivated intelligence and security services to try to use information and communication technology by indiscriminately intercepting data flows, discovering and analysing their trends in order to obtain predictive value and actionable intelligence, a huge effort that tries to protect civil society by preventing e.g. criminal and terrorist activities.
Conclusion
The introduction stated that Big Data is connected to the free flow of information and the transparency that seems to flow from it. It was said that this does not relate well to the secretive behaviour of intelligence and security agencies. Evidently, there is more to this assertion than would appear at first sight. Transparency and secrets are inextricably linked and do meet in unexpected ways.
At the core of the debate are paradoxes to which little attention have been paid within the media stream of technical possibilities and, to a lesser extent, socio-technical applications of Big Data. Recognition of the Big Data paradox will serve the purpose of an integral and more balanced perspective on the counter-intuitive, but complementary, notions of transparent and secretive behavior. If successful, all three levels of the cyber domain will be combined. Excesses on the Internet - e.g. spamming, stalking, hacking, digital fraud, etc. – required (and require) governance through regulation in order to benefit from its accomplishments. Big Data requires a comparable course of action. This awareness should translate into robust oversight data interception and, more generally, into well-organized, state-sponsored governance of Big Data flows and technologies that are revolutionizing our everyday lives.
This article is an adaptation of an article published in the Militaire Spectator (187 (6) pp. 308-323). You can find the full article here.
Dr. Alex Claver works at the Dutch Ministry of Defence and is currently a student of the Executive Master Cyber Security at Leiden University. He is an external member of the Research Group Intelligence and Security at the Institute for Security and Global Affairs of Leiden University, The Hague.

